Researchers at Duke University have developed a system that can fool automotive radar sensors into believing almost anything is possible. The technology, dubbed “MadRadar,” can hide the approach of an existing car, create a phantom car where none exists, or even trick the radar into thinking a real car has quickly deviated from its actual course. And it can do all of this without having any prior knowledge about the specific settings of the victim’s radar.
The research, which will be presented at the 2024 Network and Distributed System Security Symposium, shows that manufacturers need to take immediate steps to better safeguard their products.
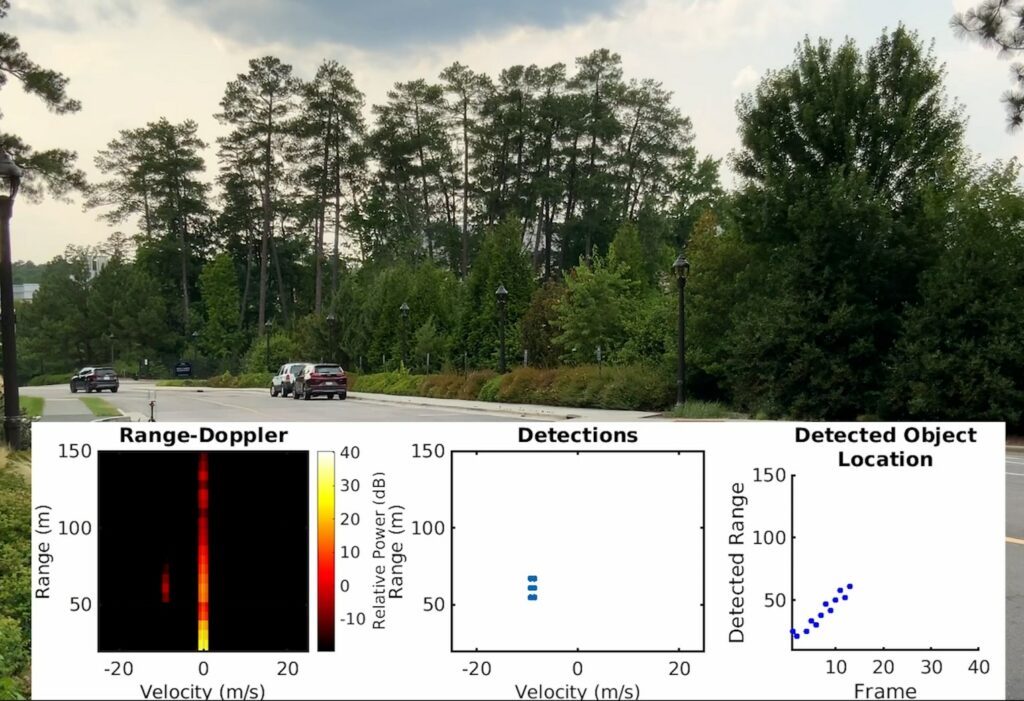
The engineers at Duke demonstrated the MadRadar system, which can accurately detect a car’s radar parameters in less than a quarter of a second. Once the parameters have been discovered, the system can send out its own radar signals to fool the target’s radar.
The problem with modern automotive detection systems is their complexity. In modern cars that feature assistive and autonomous driving systems, radar is typically used to detect moving vehicles in front of and around the vehicle.
Because there are now so many different cars using radar on a typical highway, it is unlikely that any two vehicles will have the exact same operating parameters, even if they share a make and model.
In the MadRadar demonstration, the team from Duke showed off the capabilities of a radar-spoofing system they’ve built that can accurately detect a car’s radar parameters in less than a quarter of a second. Once they’ve been discovered, the system can send out its own radar signals to fool the target’s radar.
The researchers recommend that carmakers try randomizing a radar system’s operating parameters over time and adding safeguards to the processing algorithms to spot similar attacks. If these steps are not taken, it could lead to dangerous situations on the road.
“Imagine adaptive cruise control, which uses radar, believing that the car in front of me was speeding up, causing your own car to speed up, when in reality it wasn’t changing speed at all,” said Miroslav Pajic, the Dickinson Family Associate Professor of Electrical and Computer Engineering at Duke University. “If this were done at night, by the time your car’s cameras figured it out you’d be in trouble.”
The researchers say MadRadar shows that manufacturers should immediately begin taking steps to better safeguard their products. “We’re not building these systems to hurt anyone,” Pajic said. “We’re demonstrating the existing problems with current radar systems to show that we need to fundamentally change how we design them.”
Journal Reference
- “MadRadar: A Black-Box Physical Layer Attack Framework on mmWave Automotive FMCW Radars,” David Hunt, Kristen Angell, Zhenzhou Qi, Tingjun Chen, and Miroslav Pajic. Network and Distributed System Security Symposium (NDSS) 2024. DOI: 10.14722/ndss.2024.24135
