Todays’ almost all equipment from all sectors are ‘Internet of Things’. And this number is expected to increase by 2020.
Along with this, the thing of concern is device vulnerability to hacking attacks that locate, intercept, and overwrite the data, jamming signals and generally wreaking havoc. In order to provide security to such devices, MIT scientists now have come with a novel transmitter that frequency hops each individual 1 or 0 bit of a data packet, every microsecond, which is fast enough to thwart even the quickest hackers.
The transmitter use frequency-agile devices called bulk acoustic wave (BAW) resonators and quickly switches between an extensive variety of RF channels, sending data for a data bit with each hop. In addition, the specialists consolidated a channel generator that, every microsecond, chooses the random channel to send each bit. Over that, the analysts built up a wireless protocol to help the ultrafast recurrence jumping.
Rabia Tugce Yazicigil, a postdoc in the Department of Electrical Engineering and Computer Science said, “With the current existing [transmitter] architecture, you wouldn’t be able to hop data bits at that speed with low power. By developing this protocol and radio frequency architecture together, we offer physical-layer security for connectivity of everything.”
“More seriously, perhaps, the transmitter could help secure medical devices, such as insulin pumps and pacemakers, that could be attacked if a hacker wants to harm someone. When people start corrupting the messages [of these devices] it starts affecting people’s lives.”
In selective jamming attack, hacker catches and corrupts data packets transmitting from a single device yet leaves all other adjacent devices unscathed. Such targeted attacks are hard to recognize, as they’re regularly mixed up for poor a wireless link and are hard to battle with current bundle level frequency-hopping transmitters.
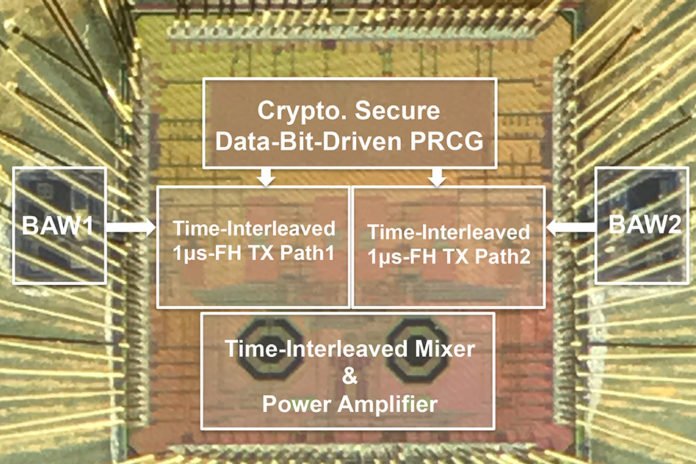
In order to develop an ultrafast frequency-hopping method, scientists primarily replaced a crystal oscillator — which vibrates to create an electrical signal — with an oscillator based on a BAW resonator. However, the BAW resonators only cover about 4 to 5 megahertz of frequency channels, falling far short of the 80-megahertz range available in the 2.4-gigahertz band designated for wireless communication.
Scientists then incorporated components that divide an input frequency into multiple frequencies. An additional mixer component combines the divided frequencies with the BAW’s radio frequencies to create a host of new radio frequencies that can span about 80 channels.
The next step was randomizing how the data is sent. For that, scientists employed a system that every microsecond creates a couple of isolated channels over the 80-channel spectrum. Relying on a preshared secret key with the transmitter, the receiver does a few figurings to assign one channel to convey a 1 bit and the other to convey a 0 bit.
However, the channel conveying the desired bit will dependably show more energy. The receiver then compares the energy in those two channels, notes which one has a higher energy, and decodes for the bit sent on that channel.
Because the channel selection is quick and random, and there is no fixed frequency offset, a hacker can never tell which bit is going to which channel.
As a final innovation, the researchers integrated two transmitter paths into a time-interleaved architecture. This allows the inactive transmitter to receive the selected next channel, while the active transmitter sends data on the current channel. Then, the workload alternates. Doing so ensures a 1-microsecond frequency-hop rate and, in turn, preserves the 1-megabyte-per-second data rate similar to BLE-type transmitters.
Peter Kinget, a professor of electrical engineering said, “Most of the current vulnerability [to signal jamming] stems from the fact that transmitters hop slowly and dwell on a channel for several consecutive bits. Bit-level frequency hopping makes it very hard to detect and selectively jam the wireless link. This innovation was only possible by working across the various layers of the communication stack requiring new circuits, architectures, and protocols. It has the potential to address key security challenges in IoT devices across industries.”
Co-authors on the paper are Anantha P. Chandrakasan, dean of MIT’s School of Engineering and the Vannevar Bush Professor of Electrical Engineering and Computer Science (EECS); former MIT postdoc Phillip Nadeau; former MIT undergraduate student Daniel Richman; EECS graduate student Chiraag Juvekar; and visiting research student Kapil Vaidya.