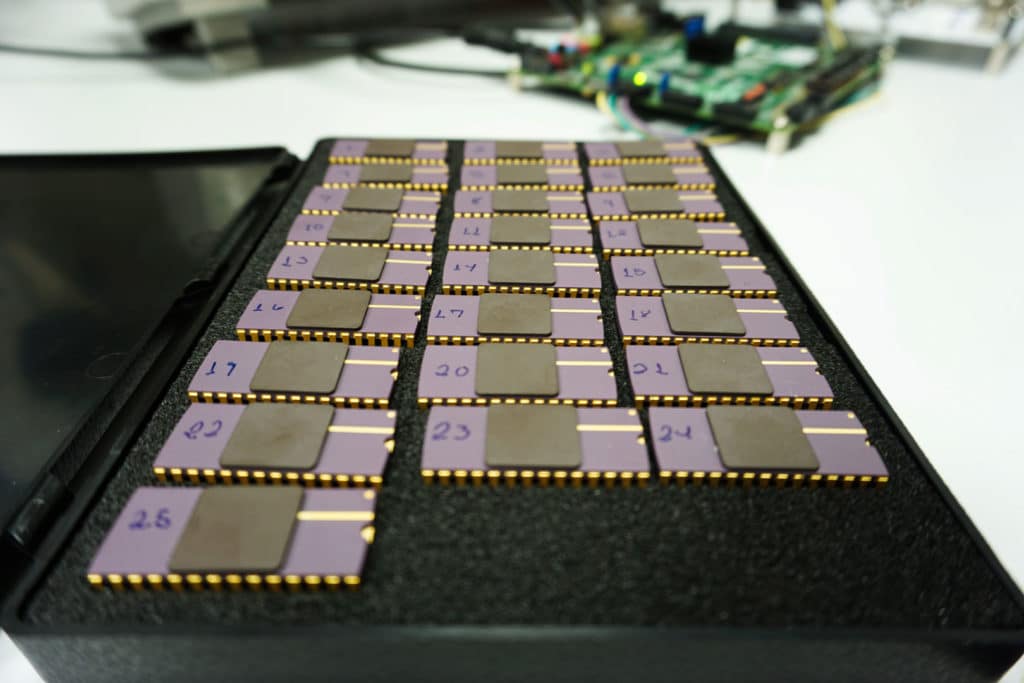
A small team of security researchers at Tallinn University of Technology (TalTech) have demonstrated that Hardware Trojan Horses can be inserted into computer chips while they are being fabricated. After the researchers finalized their insertion methodology, the entire layout manipulation to insert four Trojan Horses took just a little over one hour.
Research group have demonstrated that this type of threat is much more plausible than previously thought. “We looked at this problem from the point of view of a single rogue engineer from the chip factory,” says Professor Samuel Pagliarini, the head of the Centre for Hardware Security. “The questions we wanted to answer were about the feasibility of this attack. Can a chip layout that is ready for production still be manipulated? If so, who can do it? With what tools? How much time would it take to insert these Trojans? The only way to answer these is to pretend to be an adversary,” explains Pagliarini.
As it turns out, a motivated adversary already has access to all the tools needed to do this type of attack. “We relied on everyday software that is used to design circuits, nothing out of the box. And this is the scary part”, noted Professor Pagliarini.
An old question for the new problem
For more than almost two decades now, researchers have hypothesized that Hardware Trojan Horses can be inserted in computer chips while they are being fabricated. These Trojans are malicious circuits that typically aim to corrupt the computation being carried out by a computer chip or, in a cleverer scenario, they may expose privileged data such as keys utilized in cryptography.
Conceptually, this is considered a feasible threat given the distributed nature of the integrated circuit ecosystem. Chips are conceived by engineers working at design houses, while the actual fabrication of the chip takes place at a third-party semiconductor foundry. The designers of the chip only share a layout representation of the chips with the foundry, which is then tasked with building thousands (if not millions) of units of the chip. Here, there is a simple analogy to be drawn: the layout provided by the designers serves the same purpose of the blueprint of a house. You could think of the designer as being the architect of this house and the foundry as playing the role of the construction workers. The somewhat surreal assumption is that the construction workers are an untrusted third party; they might want to make your house collapse! Or – now coming out of the analogy – the chip factory is untrusted and might want your chip to leak some sensitive information.
Malicious modifications made by only one rogue employee

Professor Pagliarini also explains that despite large academic curiosity, there are very few works that have demonstrated the feasibility of a Trojan Horse. Previous works in this topic have a tendency to assume an infinitely capable adversary, resourceful and insightful, capable of manipulating any circuit in a number of ways. The team at TalTech adopted a more restrained (and realistic) approach: there is a single rogue employee involved in the chip fabrication and he/she only has a few hours at most to make these malicious modifications.
The PhD student involved in the project, Tiago Diadami Perez, developed a framework for inserting the malicious logic while causing minimal disturbance to the existing circuitry. The way this is achieved is by leveraging a clever feature that circuit designers have been using for many years, referred to as the ECO flow.
“When chips are sent for fabrication and an undetected bug is present in the design, there is no way to fix it. A new project has to be started, nearly from scratch. What the ECO flow gives is the capability of making small local fixes in a layout to correct these bugs, saving time and resources. What we did is the opposite: we have used this flow for inserting bugs”, says Tiago.
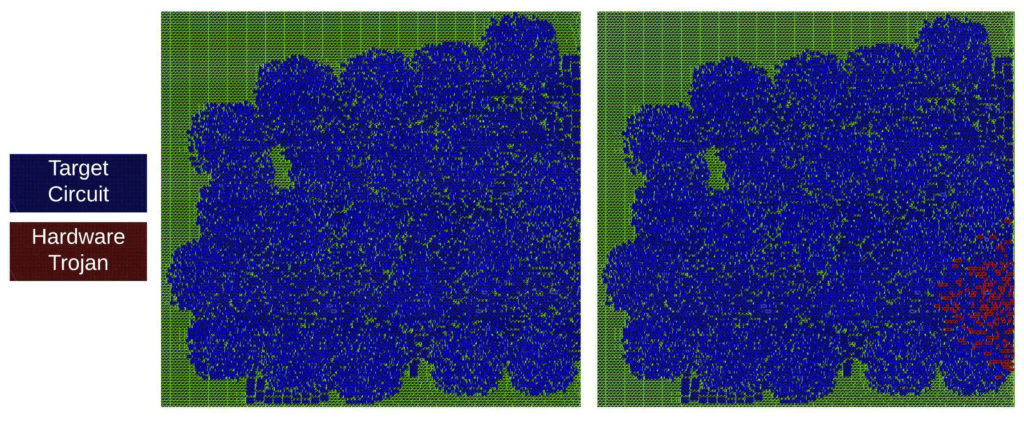
The researchers were skeptical at first, not sure if the inserted logic would fit. That is when they decided to up their game by selecting really ambitious target circuits: some very fast and very dense cryptographic circuits, AES and Present, were selected as candidates. If the Trojan Horse insertion was anywhere less than ideal, the performance of the targeted circuits would be affected and the adversary would potentially be exposed. To avoid detection, the researchers hypothesized that an adversary may decide to place the malicious logic in tiny “gaps” that exist between the components of an integrated circuit. To their surprise, they could always find enough of these gaps, even in very dense circuits. This is shown in the image below, where the red areas correspond to the malicious logic inserted by an adversary.
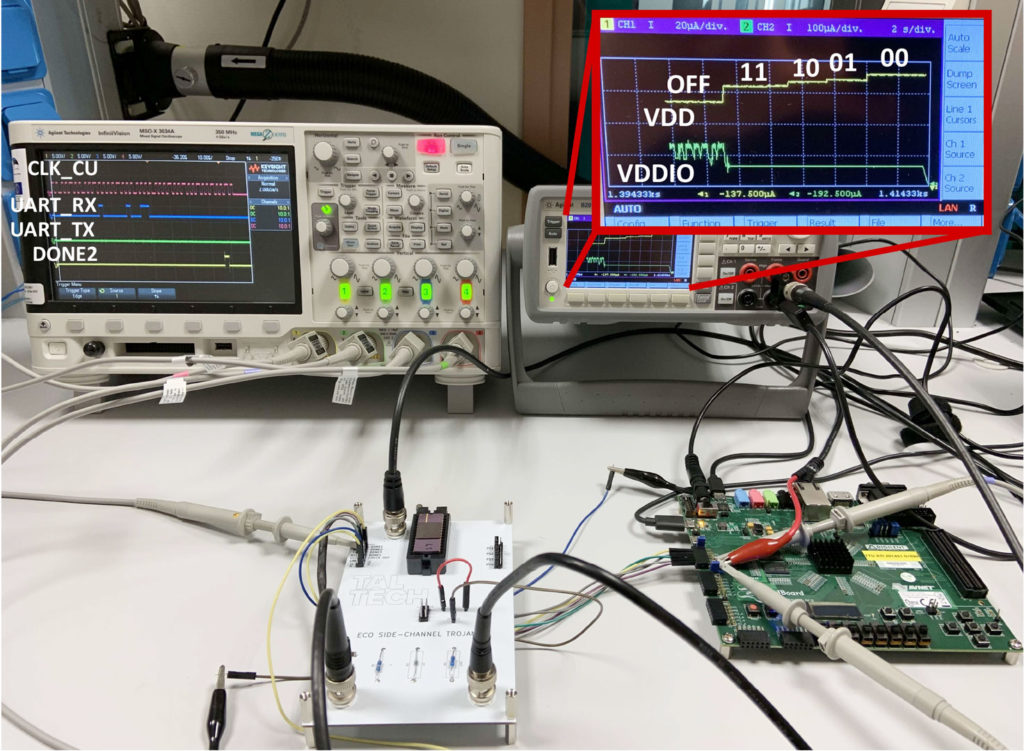
From there, the researchers decided to produce a real chip containing four variants of Trojan Horses. This process took over one year to be completed. The Trojan Horse insertion process was refined over many months and the actual fabrication took another two and a half months. When the newly produced chips arrived at TalTech, it was time to test them. Armed with some typical laboratory equipment (oscilloscopes and power supply units), the researchers confirmed the information leakage from all four Trojan Horses. In Fig. 3, the chip is leaking 8 bits (11-10-01-00) by modulating its own power consumption. All that is needed from an adversary is to look at the discrete steps to learn what the cryptographic key is, thus breaking any secure communication based on it. However, since these discrete steps are in the order of units of microwatts, an end-user would not be able to notice something is wrong with the chip.
Why chip design companies do not have their own fabrication facilities? In very short words, there is a steep cost barrier. Owning a silicon foundry is a multibillion-dollar endeavor and only a handful of foundries still compete for the title of “best silicon”. The industry has adopted the so-called fabless model, where design and fabrication are executed by different companies.
Who would benefit from a hardware Trojan Horse? There are no simple answers here. A nation-state might be interested in jeopardizing critical infrastructure of another state. A disgruntled employee might be interested in hurting the image of the chip factory or of the design company. Financial manipulation of stock markets has also been hypothesized.
How to detect hardware Trojan Horses? The hardware security community already knows that such trojans can be found if the circuit is delaminated and inspected via X-ray or scanning electron microscope (SEM) imaging. However, applying these techniques is not a common practice. Such drastic measures are either destructive or time consuming, making them only interesting if the end-user already suspects something is wrong.
What is next for the team at TalTech?
“Prevention, detection, and prevention again”, says Prof. Pagliarini. “Now that we have much better insights into the capabilities of an adversary, it is time to revisit some existing detection techniques and adapt if necessary”. The PhD student also agrees, saying that they are already collaborating with other research groups to achieve this.
For now, their ingenious chip has been accepted for presentation at a student design competition organized by one of the best conferences in their field (ASP-DAC). They hope that their pragmatic approach can shed (new) light on the topic of Hardware Trojans.
Journal Reference
- T. Perez, M. Imran, P. Vaz and S. Pagliarini, “Side-Channel Trojan Insertion – a Practical Foundry-Side Attack via ECO,” 2021 IEEE International Symposium on Circuits and Systems (ISCAS), 2021, pp. 1-5, doi: 10.1109/ISCAS51556.2021.9401481.
- T. Perez and S. Pagliarini, “A Side-Channel Hardware Trojan in 65nm CMOS with 2uW precision and Multi-bit Leakage Capability,” 2022 Asia and South Pacific Design Automation Conference (ASP-DAC UDC), 2022.
- T. Perez and S. Pagliarini, “Hardware Trojan Insertion in Finalized Layouts: a Silicon Demonstration,” arXiv:2112.02972 [cs], Dec. 2021. [Online] arXiv:2112.02972
